I understand the reasons behind but I have to say that the docs are pretty scarce and any newbie has a pretty steep learning curve ahead especially if used to the old way of configuring LDAP.
The configuration now is in ldif format and it follows a pretty logical scheme which is clearly shown in this picture
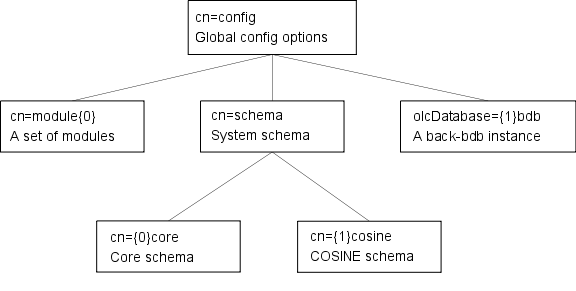
/etc/ldap/slapd.d dir) is all your LDAP server knows about, all the rest in the /etc/ldap is not really that interesting.Anyway you are to read something else, I know. I could not honestly find a straight answer to the question which gives the title to this post, even though there are a lot of places that contain bits of info but as usual the amount of work needed to get everything in place is still some. That's why I am writing this post.
[UPDATE: just found this which is pretty close to what I needed.]
I will start with a practical real-life example: Adding the sshPublicKey schema kindly provided here to your LDAP server. [I am basing my example on a Debian Squeeze installation]
Now you will find in
/etc/ldap/schema/ a lot of .schema files. And there is where you will start to get confused... so forget the schema files.Copy paste the
openssh-lpk_openldap.schema in /etc/ldap/schema/ directory (just to keep them happy together):# # LDAP Public Key Patch schema for use with openssh-ldappubkey # Author: Eric AUGE <eau@phear.org> # # Based on the proposal of : Mark Ruijter # # octetString SYNTAX attributetype ( 1.3.6.1.4.1.24552.500.1.1.1.13 NAME 'sshPublicKey' DESC 'MANDATORY: OpenSSH Public key' EQUALITY octetStringMatch SYNTAX 1.3.6.1.4.1.1466.115.121.1.40 ) # printableString SYNTAX yes|no objectclass ( 1.3.6.1.4.1.24552.500.1.1.2.0 NAME 'ldapPublicKey' SUP top AUXILIARY DESC 'MANDATORY: OpenSSH LPK objectclass' MAY ( sshPublicKey $ uid ) )
Create a tmp directory, e.g.
/tmp/ldapstuff and create a dummy file there called for instance slapd.conf which simply has this lineRuninclude /etc/ldap/schema/openssh-lpk_openldap.schema
This will create in place a dir calledcd /tmp/ldapstuff && slaptest -f slapd.conf -F .
cn=config and a file cn=config.ldif.Run
cd cn=config/cn=schema && vim cn={0}openssh-lpk_openldap.ldif
The only interesting things that need to stay in that file are the following:So remove everything else and edit dn and cn. This is a schema so it will need to be inside thedn: cn: objectClass: olcAttributeTypes: olcObjectClasses:
cn=schema,cn=config LDAP tree, so the result should be
Now you are ready to add this to your LDAP server:dn: cn=openssh-lpk_openldap,cn=schema,cn=config cn: openssh-lpk_openldap
That's it, you can verify that it's really there byldapadd -Dcn=admin,cn=config -W -f /tmp/ldapstuff/cn=config/cn=schema/cn={0}openssh-lpk_openldap.ldif
This should give you some result. This is pretty much applicable to any other schema.ldapsearch -xLLL -D cn=admin,cn=config -W -b cn=config cn=*ssh*


